
Unauthorized malware allows an adversary to hijack a device, steal data, escalate privileges, and move laterally throughout a network.
A recent example of unauthorized execution of software and its devastating impact includes the Russian hack of the Viasat constellation that brought down 12,000 internet connections and 4,000 wind turbines distributed across Europe. The hackers were able to bypass VPN and firewall safeguards which allowed them to remotely load and execute wiper malware that effectively bricked devices in the field.

To mitigate these threats, we need a line of defense for executing unauthorized firmware/software on your system. We need Hardware Root of Trust (HWRoT).
If a HWRoT solution had been implemented the attempts to upload new wiper malware to the host device would have been mitigated, to some degree, since the malware would not have been authenticated by the HWRoT.
HWRoT is a security mechanism used in system on chip (SoC) design to provide, at a minimum, the following:
The features described above enable an SoC to establish a root of trust for securely executing and updating firmware/software. Think of HWRoT as a unique identifier for a device that can be authenticated at the silicon level.
The two most common HWRoT include: trusted platform module (TPM) and platform-based silicon. A TPM can be purchased independent of an SoC or microprocessor and is generally compatible between platforms that are capable of serial protocols such as SPI and I2C.
Platform-based HWRoT are hardware features specific to an SoC. For example, there are some platforms comes equipped with silicon that enables HWRoT for an SoC. The platform specific silicon requires programming read-only cryptographic keys for enabling features such as secure boot for firmware/software.
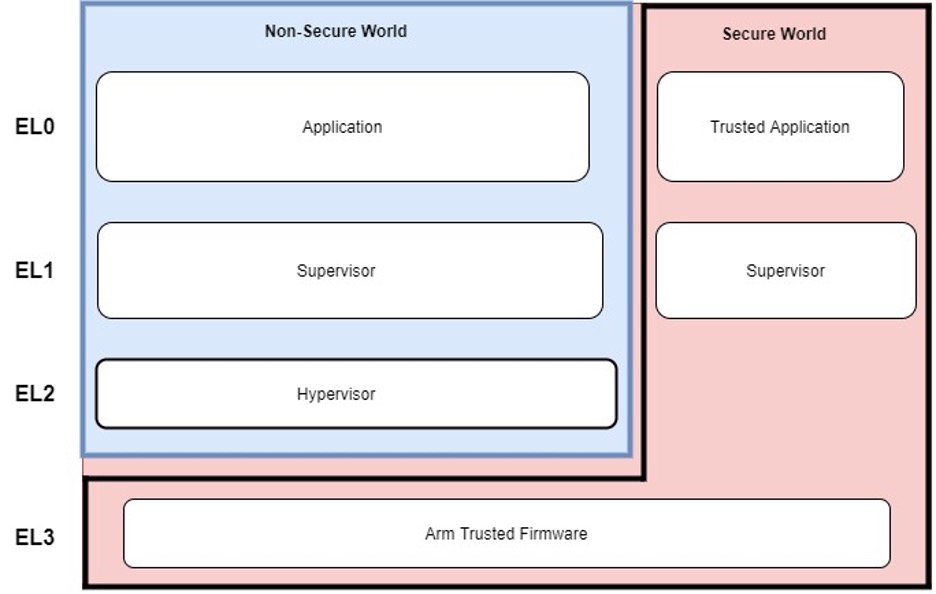
ARM TrustZone is another example of silicon-based security features that enable root of trust. ARM TrustZone comes equipped on both Cortex-A and Cortex-M processors. TrustZone provides two execution environments:
TrustZone provides a layer of isolation which enables access control to sensitive data/information that can be used for processes such as encryption and authentication. Isolation of data and code execution is only controlled by the designer. The figure below illustrates one example of the separation between Normal and Secure world on an ARM processor.
Finally, the third type is a hardware-based programmable root of trust. Programmable root of trust is dynamic in that it can be upgraded. Programming capability allows system designers to customize the device’s behavior while maintaining the integrity of the image by cryptographic signatures.
Functionality and features may vary depending on the type of HWRoT selected for a design, but, in general the functions of HWRoT include:
Secure validation and authentication: This feature is responsible for validating digital signatures produced by cryptographic algorithms. Digital signatures are a common industry practice for enabling validation of firmware/software for an SoC. An example of a common validation paradigm includes the RSA signature check. A HWRoT at a minimum would provide a mechanism to perform at least one method of validating digital signatures.
Storage protection: HWRoT solutions provide a mechanism to securely store data at rest by means of encryption and tamper resistant technology – these two methods provide a line of defense for someone utilizing advanced techniques combined with access to the hardware from inspecting the data stored on a silicon-based root of trust.
Measured/Monitored execution: This feature provides the capability to measure and verify software prior to executing during boot. Measured boot is a common practice that allows a device to securely execute authenticated software or otherwise notify of malicious software attempting to execute. In addition to measuring software executing on the system a hardware root of trust provides the capability to monitor the system in real time. Through a mechanism known as attestation a hardware root of trust can be utilized to attest/verify software at any point while the device is powered on operating in real time.
Key Management: Key management is necessary when performing authentication of digital signatures. In addition to providing a management solution for authentication paradigms, a hardware root of trust provides key management services for storing encryption keys for establishing secure communication and securing data at rest.
Implementing HWRoT is not a catch all for cybersecurity needs. While it is a good foundation to start with – it does not prevent or mitigate all attack surfaces for an SoC. The application and use case of a product are ultimately going to dictate what vulnerabilities exist for your HWRoT solution. However, one example of how HWRoT has been compromised include the hacking of Space X’s Starlink system.
This was made possible by having physical access to a ground terminal and retrofitting an SoC to attach to certain components of the Starlink hardware. Once the modified chip was retrofitted to the Starlink device the HWRoT was compromised by “glitching” the boot sequence. This ultimately led to extracting of the bootloader stored on the system as well as data stored in eFuse memory.
Even though the HWRoT was compromised in this case – further escalation attempts to overwrite and commandeer the Starlink hardware was thwarted by a GPS tether that only allowed “development” code to execute in certain geographical locations.
Whether you’re new to hardware system design or a seasoned pro the concepts surrounding cybersecurity at the embedded level can be a bit daunting. DornerWorks has the expertise in this area to help select a HWRoT solution that is right for your product as well as provide a roadmap for helping to identify and mitigate threats to your design.
Schedule a meeting with our team when you are ready to turn your ideas into reality.