
When mixed-criticality embedded systems are deployed on vehicles in the field, it is imperative that high-criticality applications such as control or engine systems can run uninterrupted despite cyber-attacks threatening to disable them. These systems will commonly provide an interface to the high-criticality applications for data collection or remotely viewing process information, and while it may be necessary, it also provides another point of attack.
In addition to the benefit of isolation provided by the seL4 hypervisor, DornerWorks has developed a cyber component that can protect the high-criticality applications from the vulnerable code in the event of a cyber threat. This will eliminate the attack vector of the malicious party and allow the high-criticality applications to run without interruption.
The cyber component consists of an additional virtual machine (referred to as the network break VM) and an seL4 userspace monitor application/component. The network break VM sits on the network in series between the incoming network traffic and the high-criticality applications, moving the direct attack surface from the high-criticality applications to the network break VM. Adding the network break VM allows different types of network inspection or memory introspection applications for determining threats and creates more variability when shutting down the interface.
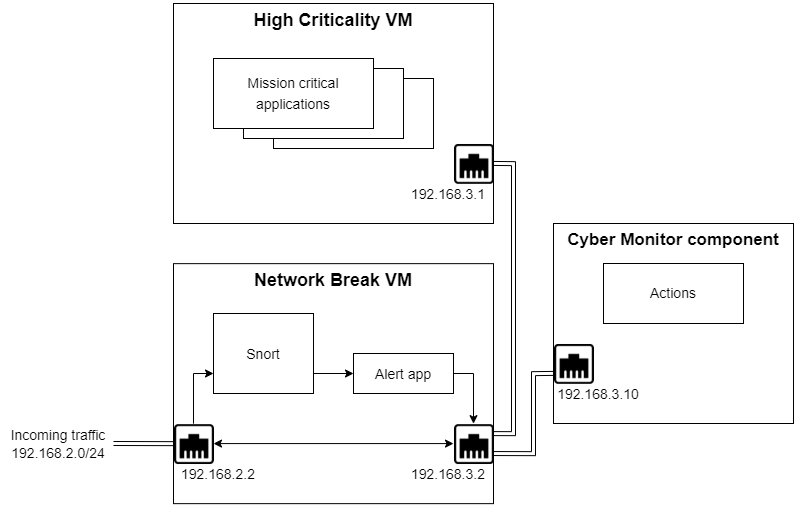
The network break VM is the element of the system that will inspect activity for malicious attacks. In the system shown above, the network break VM has an application called Snort on it. Snort is an open-source network intrusion detection system that has the capability to examine network traffic. Snort uses a set of defined rules to match data in network packets such as source/destination IP address, packet sizes, contents, or formats. Shown below are some Snort rules and explanations for what they are matching (based on the system shown above).
alert tcp any any -> 192.168.3.0/24 any |
Match any tcp traffic destined for 192.168.3.0/24 subnet (virtual network between VMs) |
alert tcp any any -> 192.168.2.2 any |
Match any tcp traffic destined for network break VM |
alert udp any any -> 192.168.3.1 any (content:”deadbeef”) |
Match any traffic destined for high-criticality VM that has the content “deadbeef” |
alert tcp any any -> 192.168.3.1 23 |
Match any Telnet (TCP port 23) traffic destined for high-criticality VM |
alert tcp any any -> 192.168.3.1 21 |
Match any FTP (TCP port 21) traffic destined for high-criticality VM |
In addition to the inspection software, the network break VM contains an alert application that will forward the alerts and the associated threat levels to the monitor component.
The monitor component is the seL4 application that can take the actions needed to isolate the high-criticality applications from the incoming attack. Based on the level of the threat the monitor can decide to do nothing, or take one of the following actions:
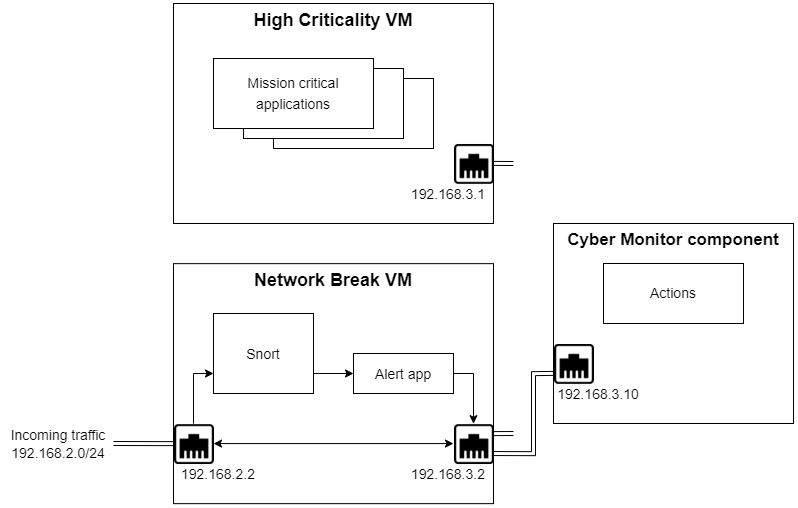
Shown below is the system with the network connection removed.
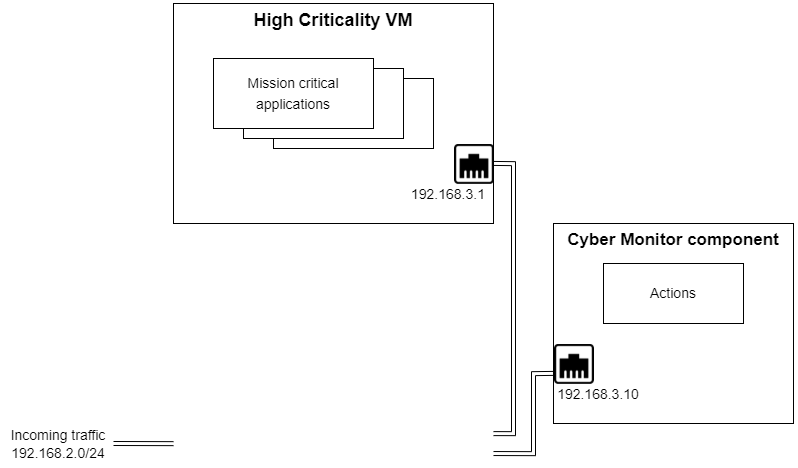
The following image shows the system with the network break VM suspended, restarting, or killed.
DornerWorks’ expertise with seL4 and mixed-criticality systems can add enhanced cyber security to your projects. Schedule a meeting with our team when you are ready for the peace of mind our secure technology solutions will give you.